Cyber Security Solutions for Industrial Operations
Securing Your Critical Infrastructure
In today’s connected world, industrial companies are continually facing cybersecurity challenges and the need to protect critical equipment. CB pacific understands, and we are here to help you best navigate through the obstacles and help industrial companies thoroughly understand the benefits and processes of industrial cybersecurity. As facilities rely more and more on connected equipment or systems, including remote access, it is crucial to secure your networks and digital infrastructure.
CB Pacific offers personalized assessments and services that provide a more well-rounded analysis of your situation to take proactive steps toward securing your critical infrastructure to help you better understand your operational industrial cybersecurity needs. Our specialists can recommend solutions that combine ease-of-use and security to allow you to get the most of your connected equipment and data-driven processes.
How Much Security Do I Need?
Download our brochure to see our risk level vs. cost matrix and learn about the right balance between cost and protection for industrial cybersecurity.
Today’s OT Systems Need IT Security Capabilities
Industrial companies require stronger OT cybersecurity programs to deal with today’s sophisticated threat environment. Managers need to invest in more advanced cybersecurity capabilities that can enable active defense of critical operations. Download this ARC report describing the major gaps in today’s OT cybersecurity programs and what’s needed for today and tomorrow’s more challenging threat environment.
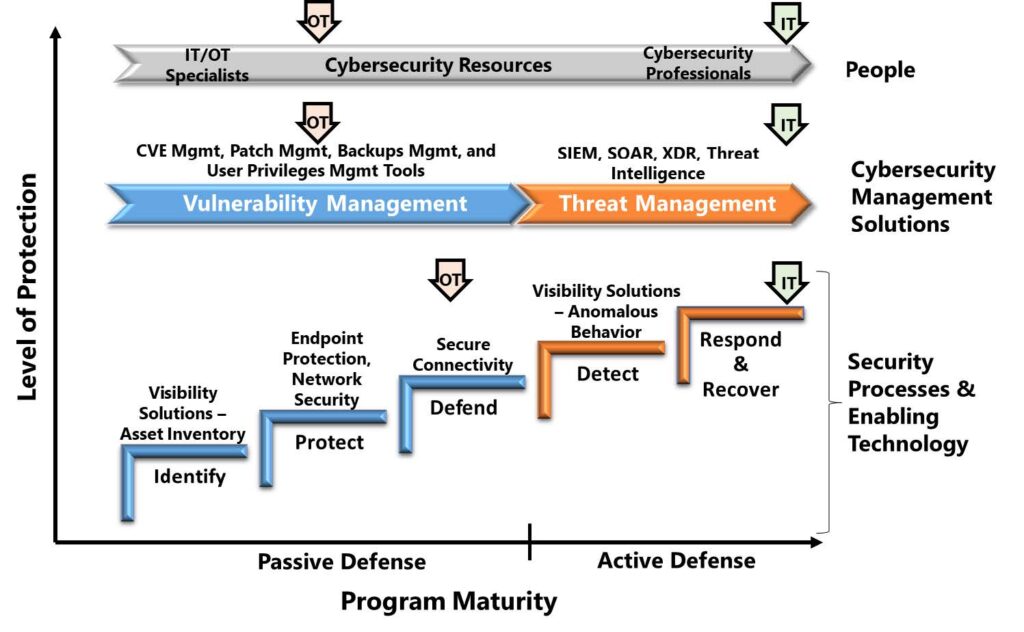
The Foundation in Helping Industrial Companies Understand and Address Cybersecurity Risks
Detect & Protect: Secure remote connectivity and/or network segmentation and isolation is important. Our experts can show you platforms available that protect against a potential breach and notify personnel about suspicious activity.
Recover & Prevent: Our experts can help you build a foundation to quickly recover and running again with version control and disaster recovery – while preparing for the future by securing data storage and creating fault-tolerant infrastructure.
Respond & Alert: Programs that issue alarm notifications in response to an event, and have security auditing and reporting, ensure you and your operation stay alert of any suspicious activity that could potentially compromise uptime.
Identify & Assess: Getting a security assessment from our experts is a cost-effective and highly productive way to identify vulnerabilities in your operation’s networks. Our experts will walk you through best practices for protecting your digital infrastructure.







